Phishing is a very common tactic with cybercriminals. Since 2017 phishing sites have overtaken traditional malware sites by more than double the peak numbers of the latter. It’s likely that you’ve either spotted or been a victim of one before. So what are the tell-tale signs of email scams, and why do so many people trust “foreign princes” with their money? Let’s talk about that.
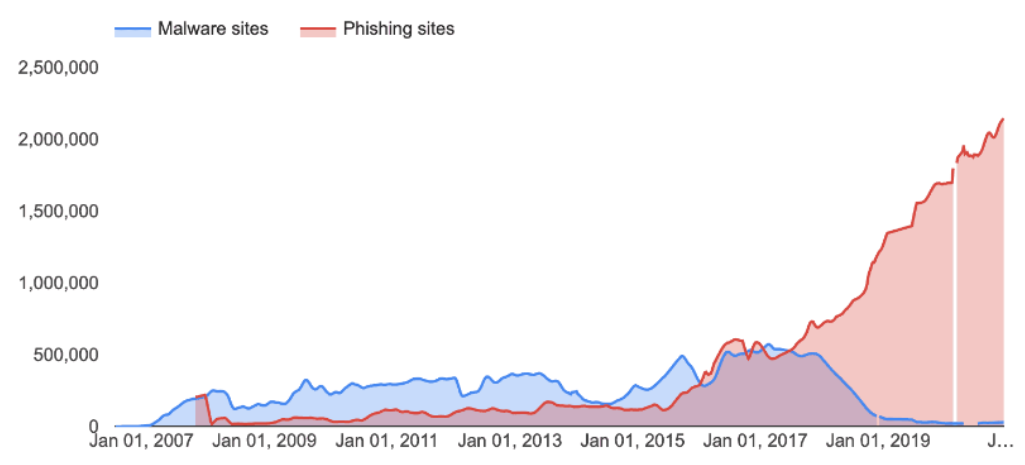
Phishing is expensive. And more common than ever. On average, and according to RiskIQ, businesses worldwide lose about $1,797,945 per minute due to cybercrime. With phishing being one of the most popular methods for attacking businesses, a large amount of that figure can be attributed to it. Being the second most expensive cause of data breaches, with an average of $4.65 million in losses per business, phishing is one of those types of cybercrime that pays to know about – even if you aren’t a security expert!
So how can we spot those nefarious emails? Here are some quick tips:
First, the obvious
One of the easiest ways to know whether an email is fake or not is by checking the contents. No, you haven’t just won £1 million from a random selection of lucky individuals. No, that one “Saudi Prince” doesn’t want to quadruple your money with a quick investment. Context is key when it comes to phishing. The phrase “if it sounds too good to be true, it probably is” rings incredibly true for a lot of email scams. Phishing attempts will often try to tempt you in a variety of ways; preying on greed, our need to help others, even our very human love of communicating with others. These types of emails, although more easily spotted, tend to aim at the most vulnerable, as they often make easy prey for these criminals.
But what if that offer the email is making looks legit? And it’s from Bill Microsoft, too! It’s time to dig a little bit deeper.
Too good to be true
On a quick peek, the email does look right – the grammar is all correct, the name on the email checks out, it even has a fancy company card at the bottom. But we’ve never met or received anything from this sender before, so we check a little further.
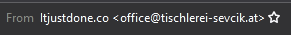
At first glance, the sender name could be legitimate, but that address doesn’t look right; and it’s definitely not someone we know. Sometimes it can be a lot more sinister; using “@goggle.com” instead of “@google.com”. It’s easy for a hacker to buy a similarly named domain for about £1 and use that to impersonate a legitimate company.
Content is also important, too. Hackers will often use a sense of urgency on their phishing attempts. By asking you to act now it attempts to stop you from thinking things through. You’ll also often find that a lot of these emails, although with correct spelling, still have bad, machine-translated grammar.
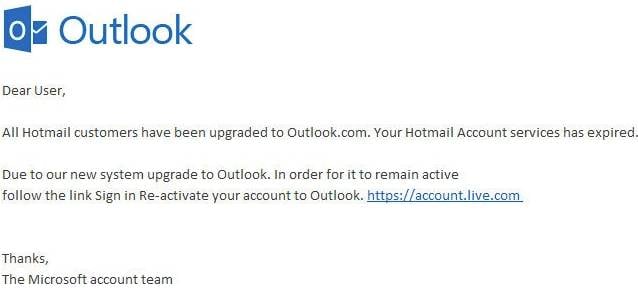
It’s clear from the image above that although there aren’t any immediate spelling mistakes, the grammar simply doesn’t flow like a professionally written email would. “Your Hotmail Account services has expired.” and “follow the link Sign in Re-activate your account to Outlook” being just two examples of poor grammar that simply would not be allowed to be sent through a Microsoft PSA.
Now we’re getting serious
So these emails so far have failed pretty basic tests. But what about an email where the sender seems legit enough, the content looks professionally done, and your initial checks seem to have come clean? Let’s think critically for a moment. This hypothetical email came from Netflix. You do have a Netflix account, you’re binging Black Mirror right now, so this email isn’t a surprise. But the email is telling you that it failed some verification, and your account is on hold because of it. Yikes! It asks you to please click on this button to follow a link, and amend the issue before it’s too late. But you’re savvy, so you check the button link before you click it.

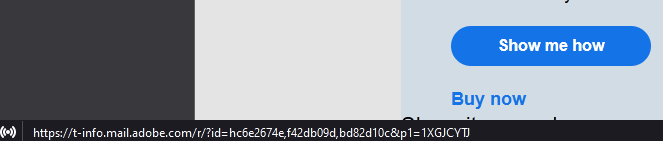
That does not look like a safe link. Interweb-billing9.com is not something a legitimate company should have as their address. The fact that it’s using a http:// link instead of the much more secure https:// format is another big red flag. Most browsers/email apps will give you the link of a button before you press it. For example, highlighting a link from Adobe gives you:
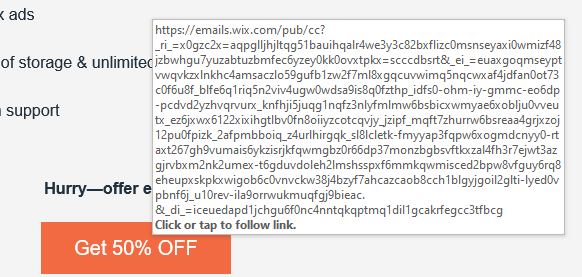
But this isn’t the end of it. Let’s say the is no button to click, but instead you are given an attachment. Once again, let’s think about it for a moment. Perhaps you know this person and their address, and it looks legitimate. But instead of clicking on the attachment we think: “why is this person sending me an attachment? Was I expecting this attachment? Does the wording of the email correlate with their usual emails?”. When it comes to email attachments, especially ones coming from what seems like a trusted source, it’s very easy to just click and forget. Attachment names, context of the email, previous rapport with the sender, a lot should be considered when opening an unexpected attachment.
The issue is that a lot of phishing attempts are never so grandiose as to announce that they have hacked you. A lot of malware works as quietly as possible. Perhaps you open a bad link and nothing changes for a week. Then suddenly, your “sent” box is filled with thousands of emails as the virus highjacked your account and managed to propagate to your entire contact list, and beyond.
Always confirm with the sender that the attachment is indeed legitimate. Perhaps you were told in advance to expect it, or maybe you’ve been having a back and forth and the attachment makes sense in context. If you have any doubt at all, it’s always safer to make sure before opening it. A lot of attachment malware doesn’t even require you to open it; simply downloading them into your system can cause serious issues.
I’ve spotted phishing on my inbox. Now what?
First of all, don’t panic. I said don’t panic!
The easiest thing to do with obvious phishing attempts that, somehow, got to your inbox instead of your Spam folder, is to rectify that and put it in the Spam folder. Chances are, like us, your webmail provider (eg Google, Outlook, etc) will take that reported email and feed it to an algorithm. From there, it will learn to identify similar patterns and help combat this type of spam.
If the email came from a trusted source but you can still tell it’s phishing, consider reporting it to the domain owner. Or the individual if you know them. Then, simply delete the email. No-one likes to have their account highjacked, and being branded as a spam domain can be very damaging both for the initial victim and the email provider.
Phishing is one of the most common and easily exploitable types of scam out there. Professionals fight day and night to combat it, but the fact that you still occasionally receive some goes to show how rampant the issue is. When it comes to targeted scams like this, the end-user truly is the first line of defence. Armed with knowledge and knowhow, you can keep yourself safe, and help make the internet a better place. Or at the very least, spot an email from a real Nigerian prince, and not another one of those fakes.
0 Comments